StackAnalyzer
Determine the worst-case stack usage of your embedded software with mathematical precision
StackAnalyzer is a tool for static analysis of safety-critical software. It automatically determines the worst-case stack usage of the tasks in your application and lets you find any stack overflows, or formally prove the absence thereof.


Stack Overflow Prevention
Stack overflow is one of the most critical runtime errors in embedded systems. StackAnalyzer helps you prevent these failures by providing precise worst-case stack usage analysis.
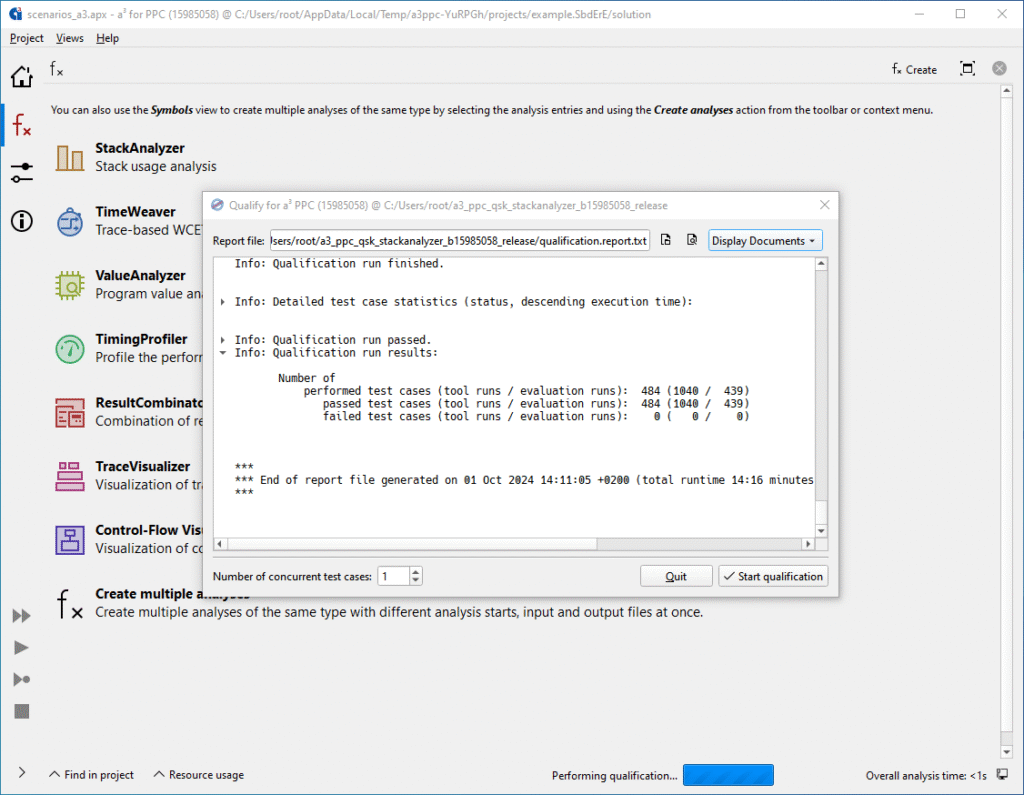
Qualification run results
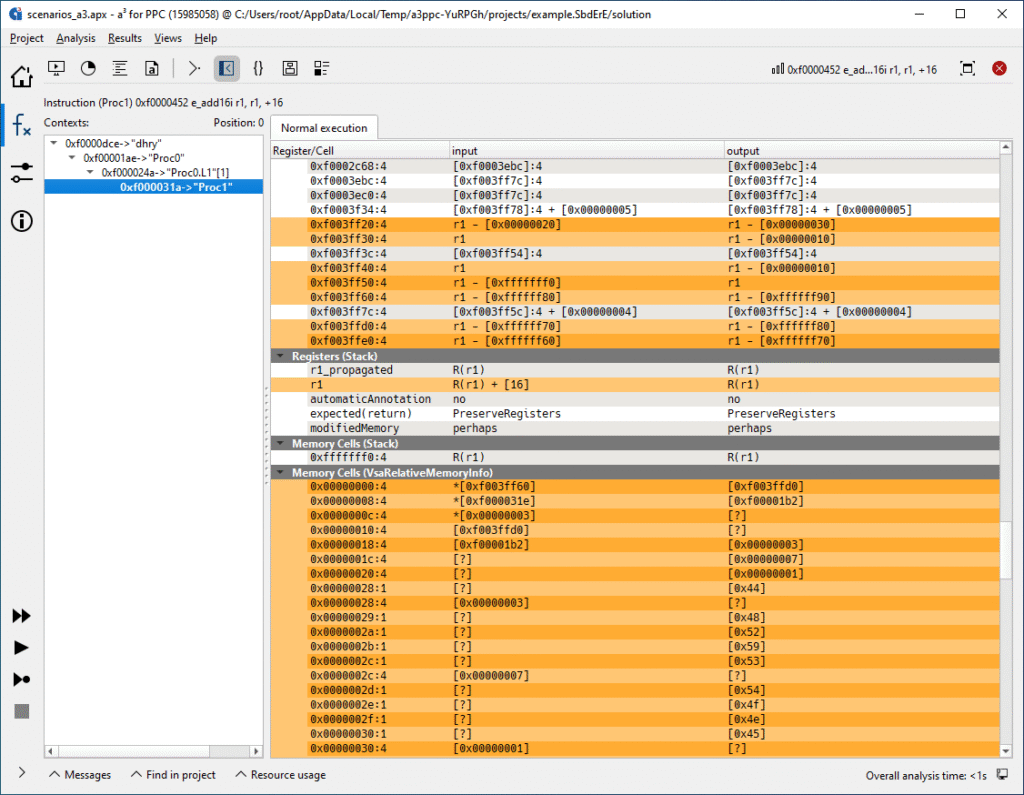
Contents of registers and memory cell
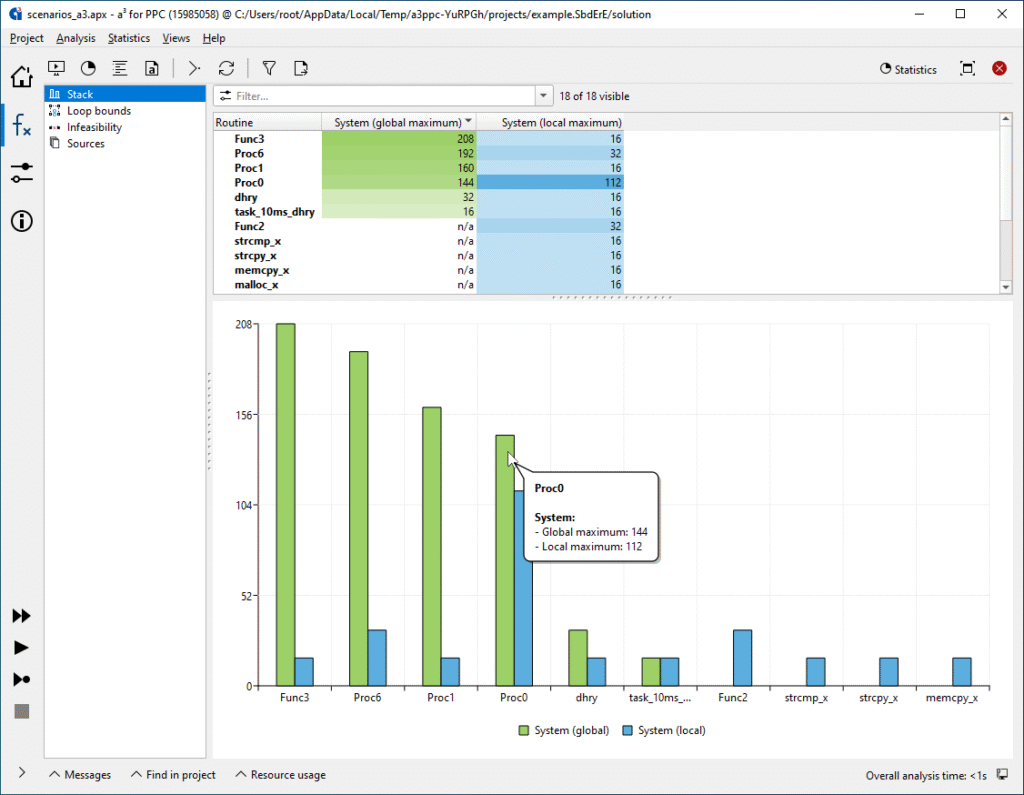
Tabular overview
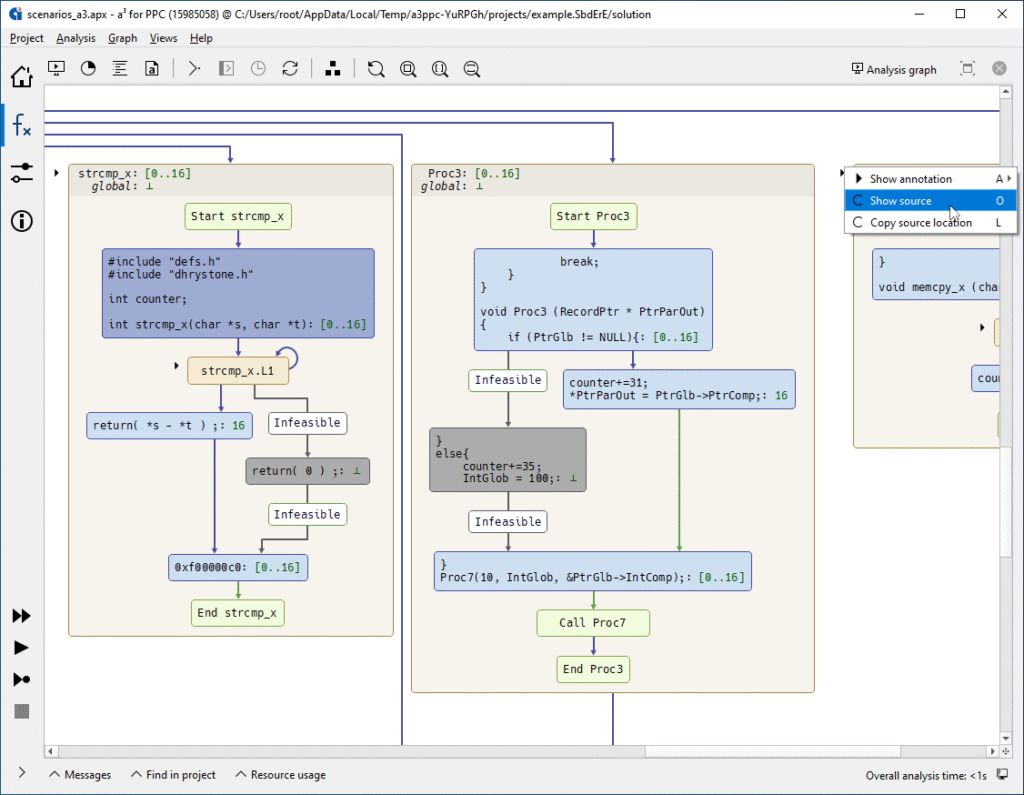
Control-flow graph
Features
Key Benefits
- Precise stack usage analysis
- Worst-case stack consumption
- Call graph visualization
- Integration with IDEs
- Supports multiple architectures
How It Works
1.Analyze Binary
Load your compiled executable
2.Build Call Graph
Construct complete call relationships
3.Calculate Usage
Determine worst-case stack consumption
Technical Capabilities
Architectures
- ARM Cortex-M, Cortex-A
- PowerPC
- x86/x64
- RISC-V
- And many more
Analysis Types
- Worst-case analysis
- Function-level analysis
- Call path analysis
- Recursive call detection
Output Formats
- Detailed reports
- Call graphs
- XML export
- IDE integration
Supported Compilers
- GCC
- GNAT
- LLVM/Clang
- Diab
- Tasking
- GHS
- Formally verified CompCert compiler, and more..
Your Benefits
- StackAnalyzer reduces the development effort and helps prevent runtime errors due to stack overflow.
- StackAnalyzer calculates the stack usage automatically. No testing or measuring required. The analysis results are valid for all inputs and any task execution.
- StackAnalyzer directly analyzes binary executables, exactly as they are executed in the final system. It requires no code instrumentation, no modification of your system, no modification of your toolchain, and it will not be confused by potential flaws in debug information.
Static analysis is a must
- Using StackAnalyzer is essential in meeting current safety standards such as ISO 26262, DO-178B/C, IEC-61508, and EN-50128, where statically analyzing the stack usage is part of the architectural safety requirements.
- CISA and FBI designate stack overflows as “unforgivable defects” that pose “unacceptable risk to national and economic security”, and urge developers to “conduct aggressive adversarial product testing, including static analysis.”
A breeze to use
StackAnalyzer incorporates two decades’ worth of feedback from commercial users and offers many helpful features, polished over the years.
- Static analysis of binary files, exactly as they are executed in the final system.
- Clear and precise information on the maximum stack usage by tasks, functions, basic blocks, and individual instructions.
- Recursions, function pointers, inline assembly code, and library-function calls are all taken into account.
- Automatic recognition of dead code.
- Exceptionally fast analysis of complex real-world software.
- Freely selectable entry points for the analysis, so you can focus on the worst-case path or other areas of interest, and speed up the analysis even further.
- Difference analysis for comparing the stack usage before and after making changes to your system.
- Customizable XML reports for documentation and certification.
- Feature-rich GUI with interactive views for analysis results, statistics, code coverage, control flow, source code, assembly code, DWARF debug info, symbol tables, configuration files, and more.
- Command-line mode for easy integration into automated build processes.
- Plugins for TargetLink and Jenkins. Fully-integrated custom builds for SCADE and Raptor.
- ValueAnalyzer add-on for static analysis of register and memory cells, memory accesses and function calls.
- Seamless integration with other analysis tools from AbsInt, e.g. aiT for static analysis of the worst-case execution time.
- Qualification Support Kits for ISO 26262, DO-178B/C, and other safety standards.
- Regular updates and excellent tech support.
Seamless integration into your toolchain
StackAnalyzer supports tight integration with state-of-the-art development tools, including:
- SCADE Suite, the market-leading embedded-software development environment from ANSYS
- Jenkins, the leading open-source automation server
- TargetLink, the production-code generation tool from dSPACE
- SymTA/S scheduling analysis tools from Symtavision/Luxoft
- RT-Druid, the Eclipse-based development environment from Evidence
- Raptor-Dev, the system-development toolkit from New Eagle
- StackAnalyzer can also be combined within a single user interface with other analysis tools from AbsInt — e.g. aiT for worst-case execution time analysis.
Qualification Support
Your usage of StackAnalyzer can be qualified according to ISO 26262, DO-178B/C, and other safety standards. We offer special Qualification Support Kits that help you simplify and automate your qualification process. These Kits are especially popular with our customers in the avionics and automotive industries.
Prevent Stack Overflows Today
Get precise stack usage analysis for your embedded applications
